 |
| It's the FBI Big-Five Personality Trait List |
Today something kinda similar happened: The Theory Is No Longer A Conspiracy.
Glenn Greenwald has access to the miles-high Snowden document archive and he and his partners are releasing it to the world through their new site: The Intercept. Today? A bomb-shell: the government (in league with the British NSA equivalent) are trying to train "Cyber Magicians" to do disinformation and manipulation on the Internet.
 |
| Think I'm Exaggerating? I'm Not Exaggerating |
All we have is the Power Point--but The Omnivore will talk to it. The Omnivore has talked to many a presentation he had no idea what was going on with.
The Omnivore Explains The Mysterious JTRIG PowerPoint
"Okay, hi. My name is The Omnivore--and--yes? Yes, for real. And I'm going to talk to you about The Art of Deception. No, what? They were hippies. Yes, that's right. Uh ... no. It doesn't fit on forms. I don't--look, Double-Oh-Seven, don't you have an island fortress to be storming or something? Alrighty then. Today I'm going to talk to you about the Art of Deception."
"Ha. Ha. Right. No, his real secret ID is George Soros."
:: Click ::
"We're with the Human Science Operations Cell" and our mission statement is to use advances in applied neurosciences, psychology, and neurobiology to enhance operational effectiveness. As you can see all this is highly classified, secret, and 'five-eyes' only (that's FVEY: AUS, CAN, GRB, NZL, and USA) so if any of this is released outside need-to-know double-ought-seven over there will have to garrote you with his watch. Ha ha. ... That was a joke."
:: click ::
 |
| JTRIG: Joint Threat Research Intelligence Group |
:: Click ::
"The Internet connects humanity in a way that no innovation in the entirety of history has previously. In order to understand and contextualize its impact on society we need to understand the scientific domains and forces that it brings to bear."
:: Click ::
We need to understand things like why a person or group rebels or complies, how individual elements of trust and personality shape the world. What neuroscience says about belief and religion--and how leadership can transform cultures and ethnicities. Just as science and the rate of communication increases in velocity so do cultural phenomena. The Internet is the catalyst for all of this potential disruption and, thus, the amplification of individual threats into something far more dangerous."
"But not as dangerous as double-ought over there, thankfully."
:: CLICK ::
"Our resources are the S4: Science, Signals Intelligence, Skills--especially esoteric ones, and Systems which we, the West, largely own and control."
:: CLICK ::
"You've already seen the logo. What? Yes--in the middle of the black pointy-thing: that's a spider. This is the World-Wide-Web, after all. What's that? CNA? Computer Network Attack. Didn't you all do any of the reading?"
:: CLICK ::
"We want to build Cyber Magicians. A Magician is a person who understands how you come to believe things and is a master at making you believe things that are not true. The nature of a magic trick isn't to fool you with some clever trick ... like a hidden wire garrote in a watch band ... but to make you construct your own narrative about what happened--a false one."
"The magician exploits holes in human perception and cognition to make you deceive yourself."
:: CLICK ::
"This class will give you accreditation in Online Covert Action. What? Yes, it counts towards continuing training. YES, it's registered with the ministry. What? Yes, fully. No--I took roll, your names will all be entered. I promise--I *promise* I won't lose it."
:: CLICK ::
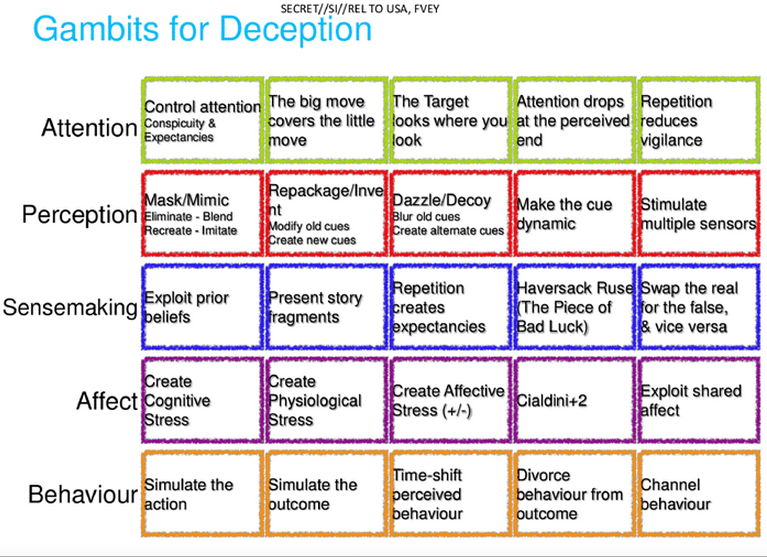
"So we have our three JTRIG areas of operation across the top and--? Oh? I ... uh ... I think Anonymous Computer Network Operations. Yes: I didn't do this slide. No, it was Bob. He's ... on assignment. I'll take a note. Thank you."
"What we see here is the three verticals and how the techniques of 'magic' and misdirection are used as we go down to have an improved impact in each space."
:: CLICK ::
"What's that? You can't? Let me zoom in."
"Ooookkay. So, the idea here is that we use the elements in white bubbles to manipulate the dynamics in the green bubbles by manipulating the concepts in the blue bubbles--along iwth performing the activities in the red bubbles ... and for the other tan bubbles? I? What?"
"No, I don't think Bob 'just learned' Power Point. No. No this is pretty scientific. Yes? In the back? I think it's--let's see ... eight point font. What's wrong with that? The purple bubbles are ... I don't ... let just ... let me just talk to this ... Okay."
"The Hofstede Dimensions are measures of a society's values. It can apply to a nation or a business or an online community. They are things like Power-Distance, how individual--especially low-power members--accept that all power in the society is not equal, masculinity vs. femininity, and--what was that? No? You were laughing. No, there isn't one for porn. No, there isn't one for power-point. Anyway ... Right--so what we are doing here is taking the temperature of an online organization or community, as it were, and then using elements like branding, social herding, and so on to influence things like performance or the media it produces."
"By being a magician we can do this anonymously and more effectively."
"Eh? Oh--uh, Paternicity and Agenticity? Those are ... uh ... made-up words, actually. They were made up by Michael Schermer who runs the Skeptic society. Paternicity is his term for the brain's tendency to see / create meaningful patterns in things and Agenticity is the human mind's tendency to believe (because of this) that there are powerful invisible agents controlling things around us."
"What? Yes ... kind of like the NSA. Right."
:: CLICK ::
"What? I--WHAT? Okay--hey! Come back here! Everybody sit down--No, I mean ... Okay, okay! Coffee break for the yanks. Right. I'll have some--Earl Gray? Sure. We'll just skip this over. It's getting in people's head--mind-space. We'll come back to that ... when Bob gets back. Promise."
:: CLICK ::
"This is what the full course teaches you. It's about three weeks, most of which is on scams and deceptions. Oh, ha-ha--yes, I suppose it's GREAT for the private sector. Yes, well, I don't know: Double-Ought is going to be killing lads for Bitcoin so you might want to try something less boring. Anyway, it's available."
"YES, of course it counts for continuing education credits. REALLY."
:: CLICK ::
"We'll skip some slides of magic and misdirection--look, here: historically magic and intelligence go way back."
"We've always had uses for misdirection, sleight of hand, and keeping to the shadows. Shouldn't be too surprising, really. Also impresses the ladies if you know what I mean."
:: CLICK ::
"The techniques work for dissimulation--hiding the real--or simulation: showing the false."
"So every one's a bit bored here. We're going to skip ahead some." :: CLICK ::
"Deception can occur anywhere within the cycle of situation awareness. Each stage and transition has weaknesses that can be exploited. Let's look at some."
:: CLICK ::
"In order to effect a misdirection you can enter the process at any of these stages and try to alter the awareness of the target. What's that? Cialdini is a professor of psychology who has written on influence--like if you make something seem scarce, you increase demand. The Haversack Ruse!? BLOODY WHAT?! You lot ought to know that!
A British Intelligence officer was chased and dropped a haversack containing the battle plans. When the Turks recovered it, the were able to fortify their positions--but it was a ruse: the plans were faked and they got overrun. Anyway, study the slide. This stuff isn't rocket-surgery."
:: CLICK ::
"These are called the 10 principles for influence but mostly they're the 7 principles for being scammed and the 3 principles of social engineering. Like, if you want someone to make a bad decision, don't give them much time--and if you do or appear to do something nice for someone the'll respond by doing something nice for you. Like that."
"So okay--we're almost out of time. A few quick hits."
:: CLICK ::
"Remember that people make decisions for emotional reasons as part of groups--not rational ones. Always control the emotions."
:: CLICK ::
"This? Oh, right--that's the Coke logo in Arabic. Brands are very important and the connotations of a brand can have dramatic impact on the Arab street. For example, this clearly says "Coke" to you. However to some Muslims it says 'No Muhammad, No Mecca'--backwards. Imagine being able to damage--or promote--a brand through judicious use of viral rumor."
"Erm, no. That was accidental. We didn't do that. It just happened. But don't ask me about Tommy Hilfiger."
"Uh-mmm Computer Network Attacks ... let me see--"
"Here we go--here are some scenarios you can run if you want to impact an organization. Let me see ... Sure--uh. No. This would all be Bob. I'm not sure. I think he's making some of these up."
"Okay. That's it. Don't forget to sign the sheet! Make sure your name is on the sheet or you won't get credit! Thank you! Thank you! ... Goodbye."
 |
| The Truth Is Out There |
Conclusions
Here's how Common Dreams (progressive) characterized the info-dump:
Using sophisticated psychological templates, the slides show how the intelligence service believes it can use subversion to disrupt online networks by using various tactics, of which Greenwald descibes two as key: "(1) to inject all sorts of false material onto the internet in order to destroy the reputation of its targets; and (2) to use social sciences and other techniques to manipulate online discourse and activism to generate outcomes it considers desirable."
I've bolded the parts I take issue with. The PowerPoint deck goes to lengths to obscure its sources (no citations, mixing and matching material, adoption of specific terms and lingo that may not apply to any serious degree to the subject matter) in order to, maybe, appear sophisticated.
But it isn't. If they are trying to create Cyber Magicians they need to invest more heavily in Shadowrun than in a three week course that spends two of it on 'scams.' However, that doesn't mean that (a) they can't flood the internet with dubious stuff and (b) they can certainly provoke some kind of reaction.
Zero Hedge, in its twice-a-day fashion, may be on to something when it notes that the inclusion of heavy-hitting trolling posts can have a measurable psychological impact on how a reader perceives a neutral article (namely, strongly worded profanity laden posts can make you perceive the down-side of a new technology as more negative). It's naive to think that a bunch of guys trying to manipulate people couldn't have any effect.
On the other hand, this just isn't Jedi-level stuff.
This document (using a generic PowerPoint template :: shudder ::) has some basic ideas on how to use cyber-operations to try to cripple a target. Here are a couple of samples:
And my favorite:
If your screen shakes now ... you know what happened. Also "no more log on" ... I guess I am kinda mad my tax dollars paid for that.
The idea that "send someone a virus" or "leak confidential information" deserves a Top Secret clearance level (look, yeah, I know it's just the template) puts in perspective just how weak this is conceptually.
On the other hand, they have tools for massive data collection, screening tools for distributed attacks, and the ability (no kidding) to send you zillions of text messages and tie up your phone. The strategy in some of these is to humiliate you by changing pictures on your social media (NO!! NOT THE BUTT CHUGGING--MY MOM IS FRIENDED!!). If they wanted to do some damage and you were on their radar ... well, they could. Of course they could: they're the Shadow Government.
In the end it isn't the obviousness of the approach, the weak PowerPoint, or the idea that they seem to have no new ideas but are in love with the ones they've adopted. No: the scary thing here is that their attempt to develop a cyber-magician capability clearly has no rational oversight. Look at that nonsense: How could it?
Attendant to that: they're already running wild. I promise you that.
Do not, for a moment, believe that a highly monetized capacity won't be used. We don't know who their targets are (activists seem to be one of the possibilities) but understand that even if these guys are just, in their heads, going after the bad-guys you could be in their dragnet. False positives are a real thing and there's clearly no one awake at the switch.
Hi guys! I welcome our new Cyber-Magician Overlords.





















I suppose this could be much worse; the awfulness of what The Man is trying to do is somewhat offset by the amateurishness of its implementation - for now.
ReplyDeleteBy the way Omni - "Patternicity" has three Ts. Just FYI.
-- Ω
I CAN MAKE UP WORDS TOO IF I WANT TO!!
Delete-The Omnivore